Background
Strong Authentication in eIDAS/eIDAS2 and Strong Customer Authentication in PSD2 are digital transactions which reduce fraud and make online and offline services more secure. Number of these transactions is increasing rapidly and it will increase exponentially in coming years. Given the global consequences and success of GDPR and eIDAS, trust frameworks like eIDAS2 and PSD2 will have a high impact on the daily lives of Europeans and beyond. eIDAS2 is expanding the scope which also mandates all EU member states to provide European Digital Identity (EUDI) Wallet to every citizen by September 2023.
The EUDI Wallets on smartphones will have following functionalities for users:
- Perform strong authentication
- Sign by means of qualified electronic signature (QES) or seal
- Let user to choose which identity attributes, data, and certificates i.e Verifiable Credentials (VCs) are shared with third parties
- Hold payment cards and perform digital payments
Qualified Electronic Signatures in eIDAS & eIDAS2
According to eIDAS 1/2 regulations, Secure Signature Creation Device (SSCD) is a software and hardware that has been implemented in a way where the user can create an electronic signature and the user has a sole control over his/her signing keys. Once these devices have been audited they are called as Qualified Signature Creation Devices i.e QSCD. Chapter 3.7 & 4 of the outline of the toolbox (which was published by the eIDAS expert group in February 2022) lists that EUDI Wallet App should act as a QSCD.
Figure 1 depicts the required key functionalities of the EUDIW app. Dotted line rounds the part of the app which contains the SSCD functionality.
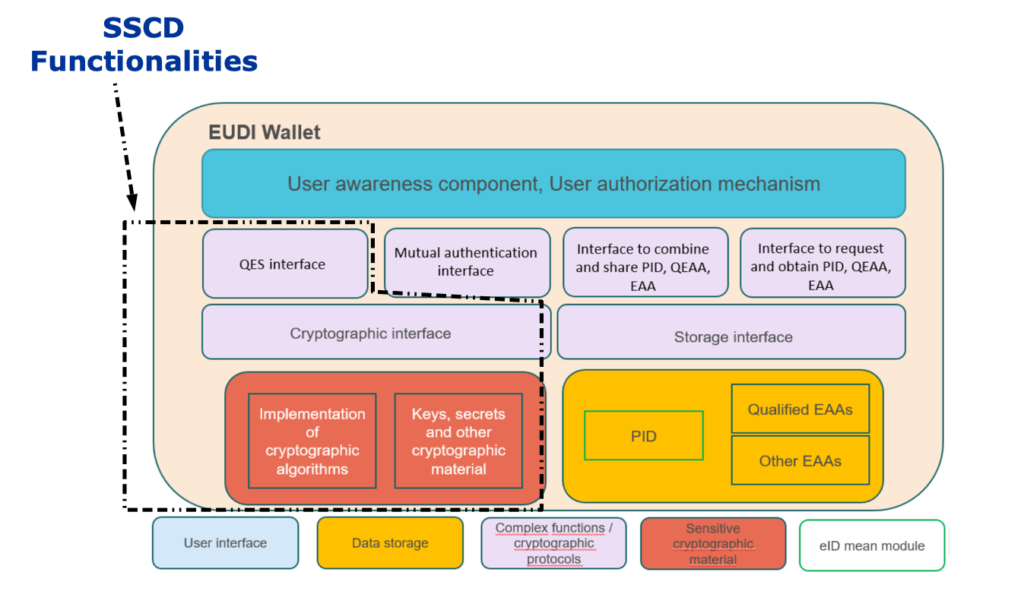
Figure 1: Proposed functionalities of EUDI Wallet through eIDAS 2
How to implement Qualified Electronic Signatures
There are many signature creation devices (having SSCD/QSCD capabilities) which can provide SSCD functionalities to the EUDIW app. There are many interfaces available to integrate these devices to the app. Many of these signature creation devices uses a common signature framework.
Figure 2 below depicts 3 tiers of strong authentication framework of signature creation devices. Creation of Electronic Seals (eSeals) use the same framework also. The first tier is the user interaction and service integration tier, which defines those actions that user sees. The second tier is those mechanisms, which the first tier uses to access secure devices. And finally the third tier are those secure signature creation devices.
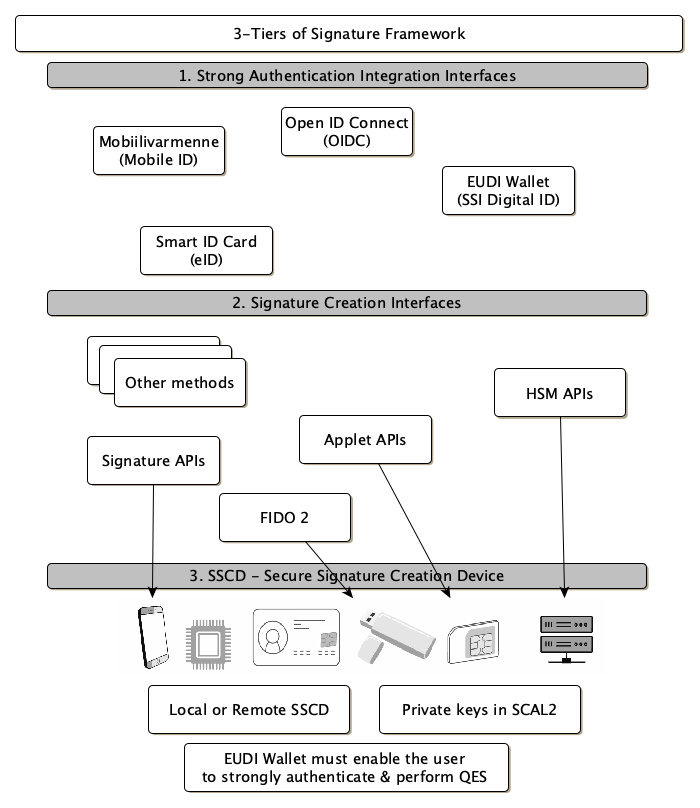
Table below lists the existing type/options for the signature creation devices.
| Sr. # | Signature creation device(s) types | Remote or Local? | Constraints & Comments | Can achieve Qualified status? |
| 1 | eID cards (smart identity cards) | Local | Does not work with phone without additional hardware | Yes |
2 | USB dongles | Local | Does not work with phone without additional hardware | Yes |
| 3 | Smartphones with Secure Element (SE) | Local | Only contained by few phones in market. | No information available on Qualified ** |
| 4 | App keystore | Local | Java style keystore for apps | No |
| 5 | Smartphone with UICC SIM Card | Local | Works on all phones | Yes |
| 6 | Smartphone with eUICC i.e eSIM | Local | Works on phones with eSIM enabled | Yes |
| 7 | Smartphone remotely connected to HSM | Remote | Remote Signing on network device | Yes |
** The Samsung S3FVRR chip provides ISO7816 interface for smartphone apps to hold secure keys similarly as in a smart card. https://www.commoncriteriaportal.org/files/epfiles/anssi-cible-2021_09en.pdf
Available QSCDs for EUDI Wallet App
According to MSS/DSS standards, there are two practical ways to implement the signature creation devices on smartphone (having SCAL2) for EUDI wallet app:
- Remote Signature Creation Device (RSCD)
- Local Signature Creation Device (LSCD)
For the remote SSCD, EU has defined a regulation of Remote Signature under eIDAS (910/2014) which utilizes European Standards (EN 419 241-1, EN 419 241-2, EN 419 221-5) to provide signature creation capabilities to the user.
However, we believe that for the local QSCD only one approach is feasible. This approach is using SIM/eSIM to hold user’s private key(s). This approach has been adopted by many member states to provide signature creation capabilities to their citizens.
As per our knowledge, there hasn’t been a single eID scheme in EU which utilizes only smartphone’s secure element/enclave (SE) to store user’s private signing keys. Currently, majority of Android smartphones do not provide SE support. Additionally, smartphone SE is controlled mainly by USA /Chinese vendors. We strongly believe that European digital identity should not be dependent on non-European vendors only. This leaves following realistic options for EUDIW App to use signature creation devices:
- Local QSCD: SIM/eSIM (UICC/eUICC) of phone to communicate with EUDIW App
- Remote QSCD: EUDIW App implementing Remote Signature service with a HSM
Image below depicts an implementation of EUDIW by providing Local or Remote QSCD by using Methics products.
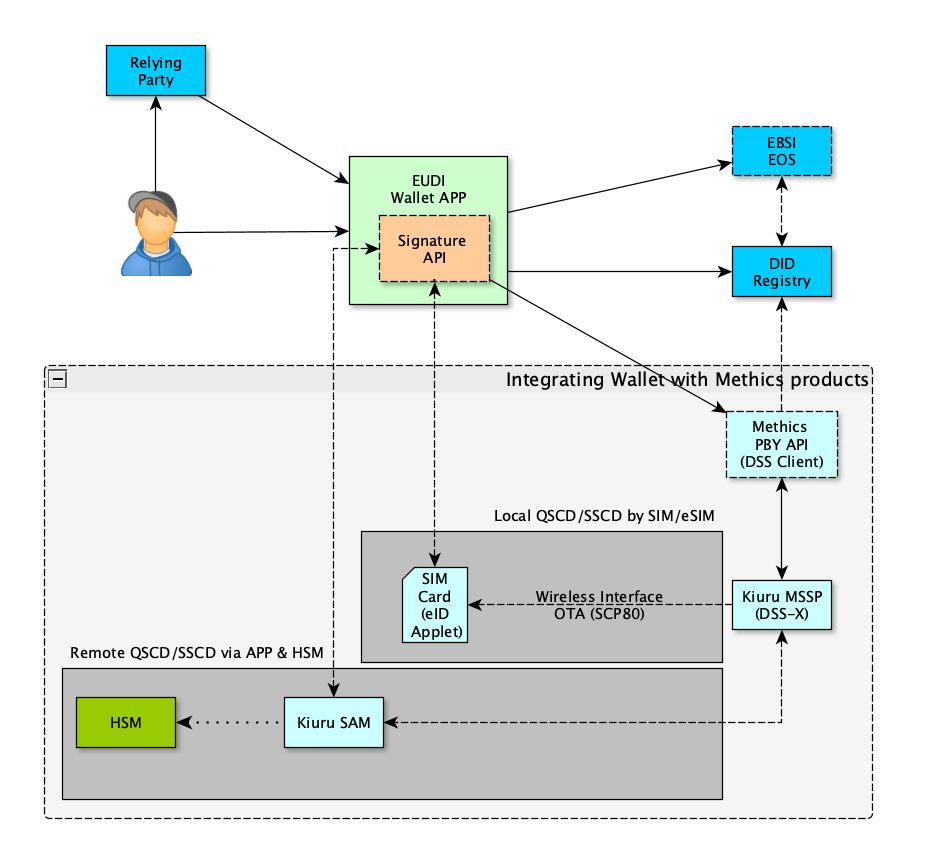
UICC/eUICC to act as QSCD for EUDI Wallet
SIM/eSIMs are well-known cost-efficient QSCDs. The SIM has an independent User interface (CAT/SAT) and a separate secure wireless interface (SCP80). We believe that SIM/eSIMs are an alternative to SE. All the technology and logistics around SIM/eSIM is mature and well tested.
For SIM/eSIM to perform QSCD functionalities, a simplified technical implementation would require installing eID applet on Supplementary Security Domain (SSD) of the UICC/eUICC.
One scenario of implementing EU wide Digital Identity could be that EU member states enter into agreements with mobile network operators (MNOs) and eID Applet vendors. Parties could make the SIM/eSIM Supplementary Security Domain widely accessible to the national Supervisory Bodies (SB). SBs can agree with local QTSPs on how to handle the eID applet logistics. This scenario has been introduced and studied also in GSMA.
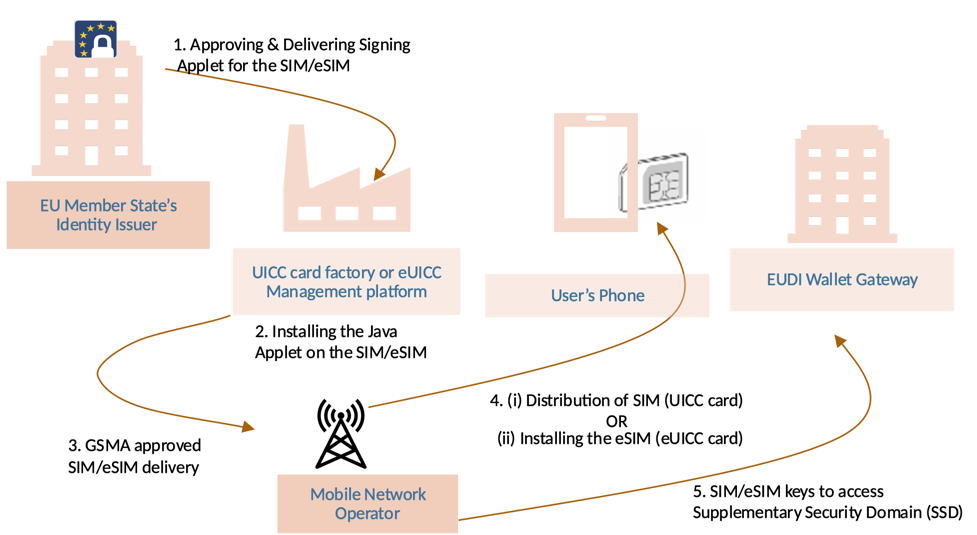
Deployment scenario of the UICC as QSCD
Member states can enter into agreements with these operators and vendors to make the PKI functionality SIM/eSIM cards widely accessible to general public. For example small national implementations (Finland, Norway, Belgium, Switzerland, etc) have been established but no Europe wide common eID applet exists for SIM/eSIMs.
eID applet could provided to the State Agency or MNO. UICC/eUICC vendor provides the SSD SCP80 keys to trusted operator or similar actors to relay signature requests to the user’s phone. Wallet issuers would use DSS-X or MSS protocols to access the eID applet. The communication with the applet is done through secure SCP80 protocol.
EUDIW will enable new roles for European network providers i.e MNOs, Applet vendors, and Wallet issuers. GSMA in their Policy note on eIDAS2 stated that:
‘MNOs are in a good position to help Member States deploy their digital wallets as quickly as possible. The industry possesses substantial assets, such as physical shops and existing digital processes for ID verification, which will allow mobile operators to help deploy digital wallets at a ‘high’ assurance level.’
‘MNOs can reach any current smartphone user with a secure element, which enables tamper-proof solutions compliant with the security requirements of this Regulation’.
An eID applet usage allows EUDIW to leverage on existing identification technologies and open standards which has been proved to be tamper-proof, secure and mature. It would provide several advantages over to remote signing and smartphone SE. Especially it would provide simple revocation, cross-border authentication and document signing features from the beginning. Moreover, it would provide SSI and eWallet functionality together with a smartphone eID app.
Currently there are many existing national Mobile ID scheme of many European countries (Finnish Mobiilivarmenne, Swiss Mobile ID, Belgian ItsMe, Sweden’s Svensk e-legitimation, etc.). Meaning every person using a mobile network have a QSCD enabled in their phone, which can be leveraged to provide QSCD requirement of the EUDI Wallet app.
How UICC/eUICC work in practice with EUDI Wallet?
One of the core functionalities of EUDI Wallet is that it can be used to receive and store digital credentials. These credentials are a part of our daily lives; driver’s license proves that we are capable of driving a motor vehicle, university degrees are used to verify our level of education, and government-issued passports allow us to travel abroad. W3C has defined these credentials as Verifiable Credentials (VC). There are three main parts of VC lifecycle:
- Registration of user
- Issuing & storing of VC
- Sharing Verifiable Presentation (VP) made out of VC
When user registers the identity wallet, the initial registration process (onboarding) registers user’s public key and DID. The onboarding process creates a PKI key pair on user’s SIM card and the public key and the identity wallet generates a unique DID. Onboarding process also loads the initial person identity credentials to the wallet. Now the user may authenticate them at any time and user has basic identity attributes to be shared.
After onboarding user needs to request VCs from university, population registry, banks etc (Credential Issuer). Each time user authenticates to Credential Issuer, user authenticates with the DID and shares the initial identity attributes issued to the DID. In this way the Credential Issuer can verify, that the user can be identified with the DID and the Issuer issues Verifiable Credentials for the DID.
The main difference between EUDI Wallet and plain ETSI M-COMM Mobile Signature Service model would be that the signature requests to the SIM card are made by the user’s wallet and not by the Application Provider (Relying Party).
New Business Models for players related to eID applet
European Digital Identity Framework needs to think of business models that are lucrative for the parties (relying parties, attestation providers or wallet providers). New business opportunities emerge for Mobile Network Operators (MNOs), UICC/eUICC vendor, platform managers, eID applet providers, and businesses who rent SSD space. GSMA in their policy note on new identity framework stated that:
‘The framework needs to consider requirements including business model considerations, that incentivise private-sector involvement such as relying parties, attestation providers or wallet providers.’
MNOs are in a good position to support European Commission to enhance the adoption rate of EUDIW. As MNOs are already subject to several identity related requirements such as KYC obligations. With use of SIM/eSIM for eID applets, MNOs can complement the national identity systems, help in issuing credentials, authenticate digital translocation, etc. MNOs can also lend the Supplementary Security domain on UICC/eUICC for a monthly or yearly basis to the EU member state government who launch Wallet for citizens and also to private businesses who want to offer EUDI Wallet offering in their app. However, this needs to examined further with relevant stakeholders.
What’s next?
eIDAS 2 laid out scope, requirements, potential building blocks, roles and actors involved in ecosystem for the EUDIW app. However, information on technical architecture & reference framework, common standards, technical specifications are not yet released. There are two major design considerations:
- How SSIs are implemented, either EBSI Verifiable Credentials or decentralized X.059 certificates
- Which type of signature creation device (QSCD) to choose
We build the case that QSCD/SSCD should be implemented locally in user’s phone by leveraging on SIM/eSIM to provide eID applet. There are many possible directions regarding the technological design of the EUDI Wallet App. However, at this point, the final choice is still unclear. So right now for technical details we can speculate, hope and anticipate the commission direction.
Methics is positioned to support the key stakeholders responsible for making the EUDIW a reality. As a global leader of open standard Mobile ID services, our products are delivering tech for strong authentication. Methics can integrate existing services and high level of assurance identity mechanisms to a new identity framework. We support digital identity over a wide variety of authentication mechanisms and security assertions. Methics will offer a bridge between traditional PKI and W3C decentralized identity projects to provide identity and signing services. Feel free to get in touch with us if you want to discuss the presented model and how SSCD/QSCD can be provided from EUDI wallet to European residents.
Publish Date: 27 June 2022
Written and Edited by: Ammar Bukhari & Jarmo Miettinen
References:
3. https://ec.europa.eu/futurium/en/system/files/ged/eidas_supported_ssi_may_2019_0.pdf
4. https://webgate.ec.europa.eu/regdel/web/meetings/2409/documents/6690
7. https://www.w3.org/TR/vc-data-model/
9. Wallet picture reference: EU Commission
